If you’re diving into the world of cryptocurrencies like Bitcoin, you’ve probably heard of Proof of Work (PoW). This system underpins how transactions are validated and blocks are added to the blockchain. But have you ever wondered about the key component that makes PoW work? That’s where a hash comes in.
So, What Exactly is a Hash?
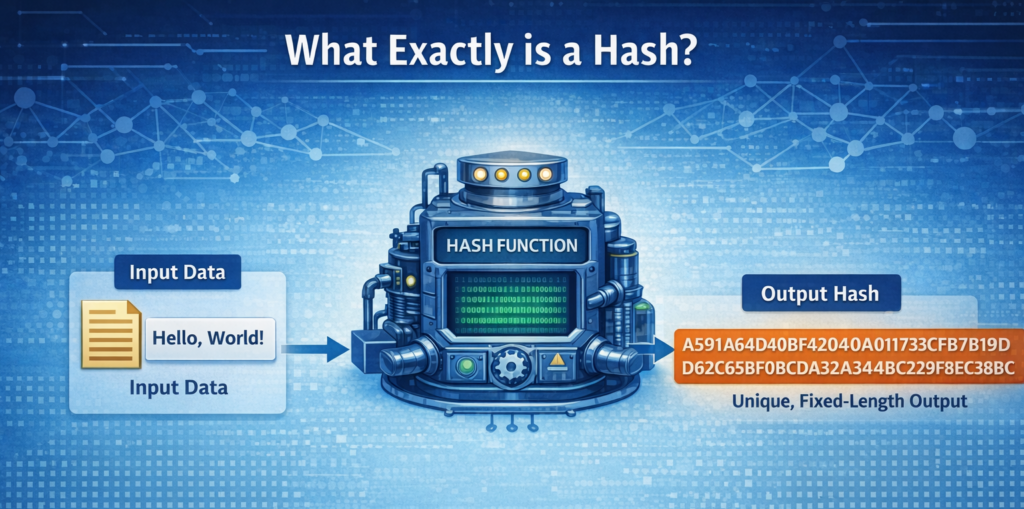
Think of a hash as a digital fingerprint. When you input data into a hash function, it gives you a unique, fixed-length output. This output is a string of characters that looks random, but it’s closely tied to the original data. Here’s the catch: even the tiniest change in the input data results in a completely different output. That’s the essence of a hash!
Some key characteristics of a hash function include:
- Deterministic: The same input always gives the same hash value. For example, the phrase “Hello, World!” will always generate the same hash every time it’s processed.
- Fixed Length: No matter how long or short the input is, the output is always the same length (e.g., SHA-256 always produces a 256-bit hash).
- Pre-image Resistance: It’s practically impossible to reverse-engineer the original input just from the hash value.
- Collision Resistance: Two different inputs won’t result in the same hash output.
- Avalanche Effect: Even a tiny change in the input (like adding a single letter) will result in a drastically different hash.
In the world of Bitcoin and many other cryptocurrencies, SHA-256 (Secure Hash Algorithm 256-bit) is commonly used. This means when data is hashed, the result is a 64-character string that’s nearly impossible to reverse.
How Does Hash Work in Proof of Work?
Now, let’s zoom in on the role of hashes in Proof of Work. The process involves solving a cryptographic puzzle, and the key to solving that puzzle is, you guessed it, hashing. Here’s how it works in simple terms:
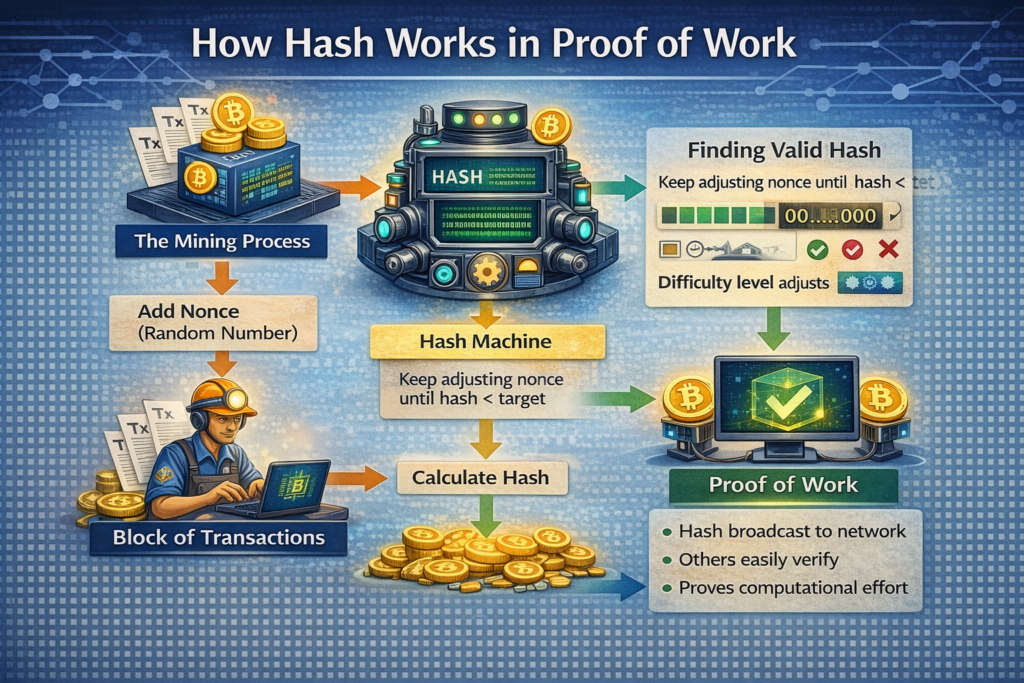
1. The Mining Process:
- When a miner wants to add a new block of transactions to the blockchain, they first gather a list of transactions.
- They then need to find a valid hash for this new block. This is where the tricky part comes in.
- The miner starts with the transaction data and adds a number known as a nonce (a random number that changes with each attempt).
- The miner hashes the block’s data (including the nonce) and checks if it meets the criteria set by the network’s difficulty level.
2. Finding a Valid Hash:
To find the valid hash, the miner adjusts the nonce, hashes the data again, and checks if the hash meets the specific condition, usually having a certain number of leading zeros. This process of trying different nonces is computationally expensive but essential.
Let’s break it down:
- The hash must be lower than a certain target determined by the network’s difficulty.
- Difficulty adjusts to ensure that blocks are added at a consistent rate (about every 10 minutes for Bitcoin).
3. Proof of Work:
Once a miner finds a hash that meets the target, they broadcast it to the network. Other participants can easily verify the hash by checking if the nonce used produces the correct hash. This is the Proof of Work: the miner has expended computational resources to solve the puzzle, proving they’ve put in the effort.
Why is Hashing Important for Blockchain Security?
This is where things get interesting. Hashing doesn’t just help miners add blocks. It plays a huge role in securing the entire blockchain network. Here’s why:
1. Immutability:
Every block in the blockchain contains the hash of the previous block. This creates a chain of blocks, and any attempt to change the data in a block will alter its hash. Since each subsequent block is linked to the previous one, changing one block would require recalculating all subsequent blocks. This makes tampering with the blockchain incredibly difficult and expensive.
2. Tamper Detection:
- If someone tries to change data in a block, the hash of that block will change.
- Since the next block depends on the hash of the previous one, altering one block creates a cascading effect, where all subsequent hashes would need to be recalculated.
- This makes fraudulent activity extremely obvious and nearly impossible to carry out without the network noticing.
3. High Cost for Attackers:
For an attacker to alter any part of the blockchain, they would need to control over 50% of the network’s computational power. This is called a 51% attack, and it’s costly because the attacker would need a massive amount of computing power to change the hashes and rewrite history.
Here’s a fun fact: Bitcoin’s network currently operates at around 500 exahashes per second (EH/s). To break that down:
- 1 EH/s = 1 quintillion hashes per second.
- Trying to overpower this network would be almost impossible without a nearly infinite amount of resources.
4. Decentralization:
Because mining is open to anyone with the right hardware, and the mining process relies on proof of computational work, PoW keeps the network decentralized. No one entity controls the entire process, and miners compete on a level playing field to secure the network.
The Dynamic Difficulty Adjustment
As the hash rate (or computational power) of the network increases, the difficulty of finding a valid hash adjusts to keep block production time constant. This means that:
- Higher Hash Rate → The system adjusts the difficulty upwards, making it harder to find a valid hash.
- Lower Hash Rate → The system lowers the difficulty to maintain consistent block times.
This dynamic adjustment ensures the network remains balanced, even as the number of miners and computational power fluctuates.
Why Should You Care About Hashing?
Understanding hashes helps you appreciate the security and efficiency of blockchain networks. Here’s why hashing matters for both miners and users:
- Security: Hashing makes it incredibly hard for malicious actors to tamper with the blockchain.
- Decentralization: By requiring proof of computational work, no single party can control the network.
- Immutability: Once a block is added, it’s nearly impossible to alter without detection.
Key Takeaways:
- A hash is the output of a cryptographic function that uniquely identifies data.
- In Proof of Work, miners must find a hash that meets certain criteria to add a block to the blockchain.
- The use of hashes ensures security, immutability, and decentralization.
- Changes in data (even small ones) drastically alter the hash, making it easy to detect tampering.
Why Hashes are Crucial
In conclusion, hashes are not just a technical detail of Proof of Work. They are the bedrock upon which the security, integrity, and trustlessness of blockchain networks rest. Without hashes, there would be no way to prove that computational work has been done, no way to ensure that data has not been tampered with, and no way to keep decentralized networks running smoothly.
So next time you hear someone talk about mining or Proof of Work, you’ll understand that behind every block added to the blockchain is a hash, ensuring that the network remains secure and reliable.
By focusing on computational work, network difficulty, and hash values, PoW creates a robust system that rewards miners for their effort while keeping the blockchain resistant to fraud and manipulation. The beauty of it lies in the simplicity of the hash, a small piece of data that carries so much weight in securing a decentralized, trustless system like Bitcoin.