Table of Contents
1. What is an airdrop?
An airdrop is a distribution of tokens or cryptocurrencies to often a large number of wallets. The coins are usually given away for free to the participants. The name ‘airdrop’ originates from the Second World War, when troops, food and equipment were distributed from an airplane using a parachute. In crypto the airdrop coins are dropped into the wallet of the receiver.
Generally, they are tokens on an existing blockchain, but they can also be coins of a new blockchain.
Airdrops can also sometimes be obtained through a so-called hard fork, which is a sort of a copy of an existing coin, explained later in this article. In the crypto community this is also identified as an airdrop.
2. What is the purpose of an airdrop?
There are many strategies behind the decision of developers to perform an airdrop. Developers have to allocate resources to successfully complete an airdrop, in time and often money. Additionally, for the distribution of a token on a blockchain there are transaction costs to be paid.
There are several reasons for doing an airdrop:
#1 Marketing
The main reason to implement an airdrop is to do so as part of a marketing strategy. An airdrop can provide brand awareness in the crypto-community, where obtaining ‘free’ coins is popular. Often there is also an affiliate (referral) program linked to the airdrop. Such a program allows those who receive the coins to invite others to join via a personal link or referral code. In return, they will receive more coins if someone signs up via their link. This can grow exponentially and thus increase awareness of the coin.
#2 Collecting contact details
Conducting an airdrop allows the developers to collect a large amount of contact information such as email addresses, Twitter accounts and Telegram accounts. These are very valuable as they connect the coin with potential buyers and other important people in the community. This is especially the case if the team is planning to raise money in a later stage using a crowdfunding method, such as an ICO or STO. This way they can easily inform participants of the airdrop about these new developments, and try to persuade them to invest in the project. The target audience can therefore be approached in a relatively inexpensive way. Using regular advertising strategies to promote an ICO or STO is difficult because Google and social media platforms, such as Twitter and Facebook, have newer restrictions against promoting ICOs and STOs.
#3 Network effect
The airdrop also can create a ‘network effect’. There is a relevant group of followers right from the start, who will advertise the coin if they like the development and progress of the coin. As soon as the coin has an official use case, many of the first participants are likely to be among this group, and a strong beginning can create immediate ripple effects. The airdrop can thus be the kickstart of a successful blockchain (service).
#4 Alternative to an ICO / STO
The laws and regulations surrounding ICOs and STOs are becoming increasingly stringent worldwide, particularly in the United States, but an airdrop can still be executed, because no money is asked in exchange for the tokens. This makes airdrops considerably less risky compared with ICOs/STOs. The financing of the project is often done in a different (more traditional) way. This could be a private sale of shares in the company instead of tokens.
3. Do you have to pay taxes on an Airdrop?
When it comes to cryptocurrency airdrops, a crucial question arises: Are they taxable? In the USA, the IRS views airdrops as a taxable event. This means if you receive new tokens through an airdrop, they are considered ordinary income and must be reported on your tax return. This applies even if you don’t receive a 1099 form for the transaction. For detailed guidance on managing ‘crypto taxes’ and IRS-related specifics, check out this resource on crypto taxes. It’s essential for U.S. citizens dealing with cryptocurrency airdrops to understand these tax obligations. Keep in mind, that tax regulations may vary in other countries, so it’s important to consult local laws for accurate information.
4. What types of airdrops are there?
#1 Unsolicited airdrop
These just appear in the participants’ wallets. If you see unknown tokens appearing in your wallet or on your ‘address’ in the blockchain explorer, you have received an airdrop.
The screenshot below is an example of such an unsolicited airdrop. What is striking is that the name of this token is a domain name (1). This airdrop is clearly a marketing method in the hope that users will visit the website.
What is also striking is that the total supply is astronomically large (2), so there is no chance that the airdrop will have any value. This is a very large airdrop to over 77 thousand Ethereum wallets (3). Most tokens don’t have that many holders.
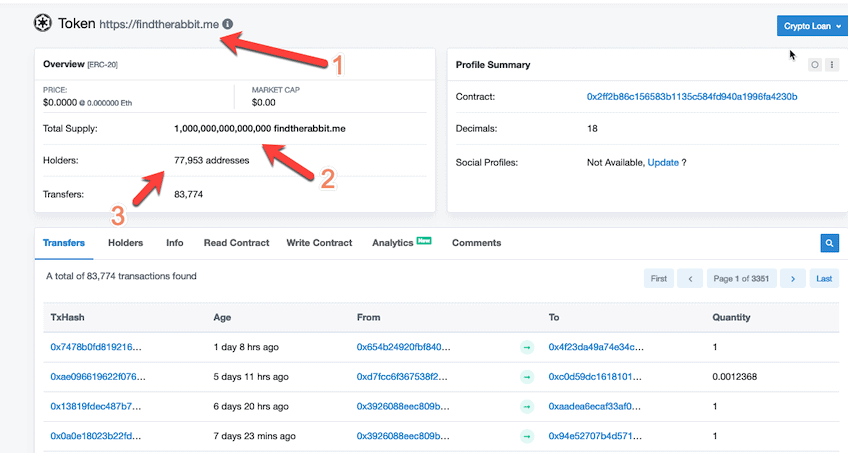
Source: etherscan.io
#2 Self-initiated airdrop
Perhaps the best type airdrop of any value is to self-initiated, and this is also the most common method. This is when the participant signs up or initiates the airdrop transaction and receives the coin or coins into their wallet. There are currently two variants:
![]() Reward for performing a task
Reward for performing a task
Participants initiate these airdrops by performing a task, such as subscribing to a newsletter. Read in this section more about the different ways to get an airdrop.
Often this method will be used for a new blockchain or token, which has not yet been created. After completing the task, they will then be on the list of participants who are entitled to the airdrop.
An example of such a new blockchain airdrop is Ontology:
“There will be no public sale of ONT. Those who subscribed to our newsletter will receive 1000 ONT for free. The details of token distribution, including the date, will be confirmed at a later date.”
![]() Enjin Beam (QR-code)
Enjin Beam (QR-code)
In 2018, the company Enjin developed a completely new method for distributing ‘blockchain collectibles’. These are a special kind of tokens on the Ethereum blockchain. These can be made by anyone and distributed using a QR code. If you scan these with the camera of your mobile phone, you will receive them directly into your Enjin wallet. The collectibles can have their own value because of the functionality they have in a game. The collectibles can be traded and the less common an item is, the higher the item’s value can be. Each collectible also has a value locked in the form of ENJ tokens. These can be extracted whenever you want, by destroying the collectibles in the wallet, after which the locked up ENJ tokens will be available.
This introduction shows how the system, called ‘Enjin Beam’, works:
#3 Claimable Airdrop from a Hard Fork or Snapshot.
Sometimes new coins can be claimed based on coins you own. This can be achieved by a hard fork or a snapshot. In the crypto community these are also called airdrops. There are some risks associated with this. The risks are laid out in this paragraph. So it is important to pay attention when claiming coins!
Hard fork airdrop
The term ‘hard fork’ actually refers to a blockchain upgrade. Each participant of the blockchain network, the miners and stakers, must use the latest version of the software within a certain period of time. If a large majority does this within the agreed time, the upgrade is successfully completed and implemented.
However, there are cases where the upgrade is accidentally or sometimes even deliberately not executed by everyone. This can happen when there is disagreement in the community or when a part of the community is not aware of the upgrade. This will cause a fork in the blockchain. Then, the two blockchains are operational separately: one with the old software version and one with the new software version. The result is that two coins are created, of which the original remains the largest. Confusingly, this phenomenon is called a ‘hard fork’, but it is sometimes also referred to as a ‘chain-split’.
Two well-known hard fork airdrops:
The first high-profile example of a blockchain split can be found at Ethereum. In 2016 there was a hack in the smart contract of the DAO token. A value of USD 250 million was stolen in Ether. After extensive discussions, the Ethereum Foundation decided to put the blockchain back in time.
Because Blockchain transactions are by definition immutable, part of the Ethereum community disagreed with this decision. Some of the miners kept the original blockchain in place, creating a split. The split-off blockchain was named Ethereum Classic. Everyone who owned Ethereum at that time, automatically received the same number in Ethereum Classic. The original Ethereum blockchain continued under the same name and was still the main chain, so nobody lost anything in their ETH and token holdings. However, Ethereum Classic has in this way become a brand new blockchain with it’s own development team and it’s own tokens.
In 2017, the Bitcoin blockchain became more mainstream and was used increasingly intensively. As a result, if you didn’t pay high transaction costs, the transaction would be confirmed less quickly. Each block in the Bitcoin blockchain is around 1MB, in which the transactions are stored. With intensive use, such as at the end of 2017, this space is not enough. This problem can be solved by increasing the size of the blocks, so that more transactions can be stored per block. This proposal led to enormous discussions within the Bitcoin community and no agreement/consensus was reached. As a result, part of the community decided to split away from Bitcoin and immediately increase the size of the blocks to 8MB. On August 1, 2017, part of the Bitcoin miners focused their computing power on the Bitcoin Cash software. This created a hard fork and the new Bitcoin Cash blockchain was a fact.
Again, every Bitcoin owner at the time of the fork can claim the same amount in Bitcoin Cash. A year and a half later, a dispute arose within the Bitcoin Cash community, which was then split off. Bitcoin SV was then created. This means that as a Bitcoin owner you are totally entitled to two new coins within two years! The ‘hard fork craze’ was really going strong during this period and many more hard forks have emerged, such as Bitcoin Gold, Bitcoin Diamond and Bitcoin GOD.
Snapshot airdrop
Sometimes you are entitled to new coins based on coins you already hold. This is done by means of a blockchain snapshot. This means that the team behind the new coin chooses a certain block from the Bitcoin blockchain. The balance of bitcoins per wallet address at that moment will be used for the airdrop distribution.
An old example of this is Clams, which was developed in the summer of 2014. The makers used a special distribution method. They distributed the coins based on the available balance of Bitcoin, Litecoin and Dogecoin. If you owned one or more of these coins on May 12, 2014 and still have the private key or wallet, you can still claim a number of Clams. The goal was to distribute the Clams as broadly and wide as possible in the crypto community.
Similar methods have been used since then, such as Ontology coins for NEO holders or Bitcoin Confidential for Smartcash holders.
5. How do I get coins via an airdrop?
These can generally be obtained in exchange for performing a task or by owning certain coins.
Some examples:
- Subscribe to a newsletter.
- Follow the coin on social media.
- Become a member of a Telegram group.
- Share a tweet or Facebook post with your followers.
- Invite people to use an affiliate / referral link.
- Create content about the coin, such as a blog post or youtube video.
- Install a (mobile) application.
- Tokens can be airdropped into your wallet without being asked, because you already have other tokens in your wallet.
- New coins can be claimed using your private key, which belongs to another coin.
For the hard fork and snapshot variant you generally have to hold the private keys yourself to get the airdrop, but in the case of large airdrops or well-known coins a crypto exchange sometimes facilitates this process as well.
Unsolicited airdrops are always tokens on a certain blockchain. If you have a wallet of them, you can see new tokens appear at any time. You often have to have some coins in order not to be skipped. At Ethereum the minimum can be set to 0.1 Ether for example. The person who performs the airdrop is only trying to reach the holders of active wallets.
Often a hard fork or snapshot airdrops requires an action on your ‘private key’ to be able to claim the new coins. So it is very important to handle this carefully. Read more about this in the next chapter.
ATTENTION: never give your ‘private key’ to an airdrop on a website or anywhere else. The chance that your coins will be stolen is almost 100%.
6. What are the risks of airdrops?
Airdrops are very popular in the crypto community. There are always people looking for free coins that can be worth a lot of money later on. Unfortunately, this is also the reason why there are people who try to take advantage of this group.
The dangers are as follows:
#1 Identity fraud
Despite the fact that an airdrop is not an ICO, KYC/AML is sometimes used. This is the abbreviation for ‘Know Your Customer / Anti Money Laundering’. This is a process carried out by financial institutions to combat money laundering. You will then be asked for all kinds of personal data, such as address details and a copy of your identity card.
You have to be very careful when you are asked to provide such information during an airdrop. It is often difficult to control how your private data is used. It can certainly happen that this information is sold on marketplaces, which can then be used to commit identity fraud. It can also be used to use your data for the KYC process of other exchanges or ICOs. This is of course very undesirable.
#2 Social Media permissions
Nowadays it is increasingly possible to use your social media account to log on to websites or apps. There are also all kinds of services that you can integrate your social media accounts with, for example, you can link your Twitter account to get analyses or to schedule Tweets. As soon as you connect your social media account, the website or app will ask permission to get certain rights to your social media account. This can vary from viewing your friends, reading your public posts, posting a post or even viewing private messages.
In case of an airdrop you are often asked to share a message with your followers or to log into an airdrop portal. In such cases, permission may be requested. You have to be very careful if this is mandatory, and if you can’t do anything else, make sure you check what rights are being asked for. Creating a dummy account is the safest option. Usually these rights are not necessary for the airdrop at all, the only purpose is to collect as much data as possible from you and to abuse your social media account at a later stage. This can be done by posting malicious links without your knowledge, but with your permission.
#3 Collecting data
Collecting data goes beyond collecting social media data. It is very common for airdrops to ask all kinds of questions before you are entitled to the coins.
This often starts with your name, social media account and wallet address for the airdrop itself. Sometimes it goes much further and asks for much more personal data, such as gender, age, address, hobbies and interests.
It often ends with the option to invite your friends by mail, so you can receive more coins when they also register. With this information, a very large set of data about you, your friends and their friends can be built up.
You won’t immediately experience any problems around the airdrop, but this can certainly happen at a later stage. You can assume that your data will be sold, and then you will be contacted by mail, telephone or even at your front door.
#4 SPAM and Phishing
If you participate a lot in airdrops and ICO’s it is almost certain that you will receive unwanted emails, i.e. spam. These will be focused on your interests and will contain some of your information to make it appear more legitimate. This can be anything, such as a fake email from Microsoft, Apple or your bank and it will also often contain phishing links.
It can also just aim to make you experience FOMO (fear of missing out) by giving you an ‘early bird’ bonus at a popular ICO. This could just be a scam ICO with the sole purpose of stealing money.
#5 Theft of crypto assets
In the case of a credit card, misuse is often reimbursed by the publisher, and at a bank there are possibilities to reverse a debit note. In the case of cryptocurrency you are actually your own bank. If someone gets access to your ‘private key’, you almost always lose the balance and you have nowhere to go to get it back. Also, a bank transfer, which you have executed yourself, can no longer be reversed. Of course it is possible to report a theft or a scam, but the police can’t really do much.
Some examples of theft:
Send Crypto to get more back
On twitter there are active bots that pretend to be famous people and promise that they will send you coins if you send them a little bit first. The bots are so advanced that even responses from other accounts are placed under, thanking the ‘person’ and that the transfers worked. Never fall for this!
In fact, this fraud happens so often that famous people in the crypto world even warned about it in their Twitter name and tagline, like Ethereum’s founder, Vitalik Buterin:
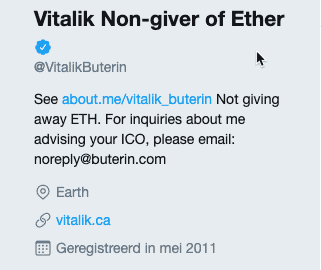
Source: Twitter
Private keys on the internet
Malicious people try anything on the internet to convince you to fill in your ‘private key’ via an (airdrop) form, private chat, a Telegram bot, or whatever else they can think of. If you do, you can assume that your coins will be gone almost immediately.
Under no circumstances should you give your private key to anyone else! Not only for an airdrop, but also not with friends or acquaintances, support departments of companies, or anyone else!
Private keys in wallet software
In case of a blockchain fork or snapshot you will almost always have to work with the software of the new coin to claim it. This means in practice that you have to enter or load the private key if it is a file (usually wallet.dat).
This mainly entails risks if there is still a balance of the original coins in the wallet. For example, there have been ‘hard fork’ scams on Bitcoin, where the Bitcoin private key is sent to the makers by the rogue wallet software. This means that the airdrop claim can cause you to lose all your bitcoins. The rogue wallet software can even look for other private keys or files on your computer.
7. Five tips to prevent losses!
As mentioned before, it is extremely important never to give up your private key. In case of a snapshot or hard fork this is a bit more difficult. These tips are especially for situations where software or browser plugins are involved.
Tips:
- Always move the original coins to a new wallet first.
- Claim the airdrop in an isolated environment, such as an old laptop or virtual PC.
- Read the experiences of other users on social media, forums and chats.
- Wait until hardware wallets and exchanges support the airdrop.
- Make sure your computer is up to date with all (antivirus) updates.
8. How lucrative is an airdrop?
Exactly how much an airdrop delivers varies enormously. Usually it’s only a few euros at the most and it also depends very much on the moment of sale. Sometimes it can be very lucrative. Here are some examples based on their all-time high (ATH) price:
![]() Ontology
Ontology
1000 ONT airdrop for subscribing to the newsletter. At ATH this was worth more than $11,000.
![]() Bitcoin Cash
Bitcoin Cash
This was a hard fork that gave you one BCH for every BTC you owned. At ATH this was worth over $4355.
![]() Hydrogen
Hydrogen
A minimum airdrop of 222222 was given to developers, who registered during the roll-out period. At ATH this was worth over $3300.
![]() Polymath
Polymath
An airdrop of 250 POLY was done after registration including KYC. At ATH this was worth over 400 dollars.
9. Where can I find upcoming airdrops?
There are several websites that maintain information about new and existing airdrops and where airdrops are announced. If you search for ‘airdrop calendar’ on Google, you immediately get a number of results.
New coins are usually announced on https://bitcointalk.org/, which often includes information about airdrops and bounties in the corresponding threads or chat channels, such as Telegram and Discords.
TIP: Join the Blockspot.io Announcements Telegram to be the first to find our airdrops!
The QR codes for your Enjin wallet are distributed in many places. This often happens in the Telegram of game developers, but also on Youtube or just in the games themselves. In this Telegram channel, the QR codes are also regularly shared, but they are then used up quite quickly.
10. Conclusion
Airdrops can be a lot of fun to join. You are in the middle of the hype and come into contact with fellow enthusiasts. However, it can take a lot of time to get involved, especially if you have to do bigger tasks like working with software and plugins.
The question always remains whether it is really worthwhile to spend so much time on airdrops. Assess by airdrop how much enthusiasm there is, what the total supply will be, whether there will be an ICO later on and how serious the team is. Check out the website and assess it for professionalism and completeness of information.
An airdrop can be very lucrative, as can be seen in the examples above. However, most airdrops are limited to a few euros. Do not be guided by FOMO, but remain critical and alert. There are many scammers active and there are many dangers lurking, as hopefully has been made sufficiently clear by now.